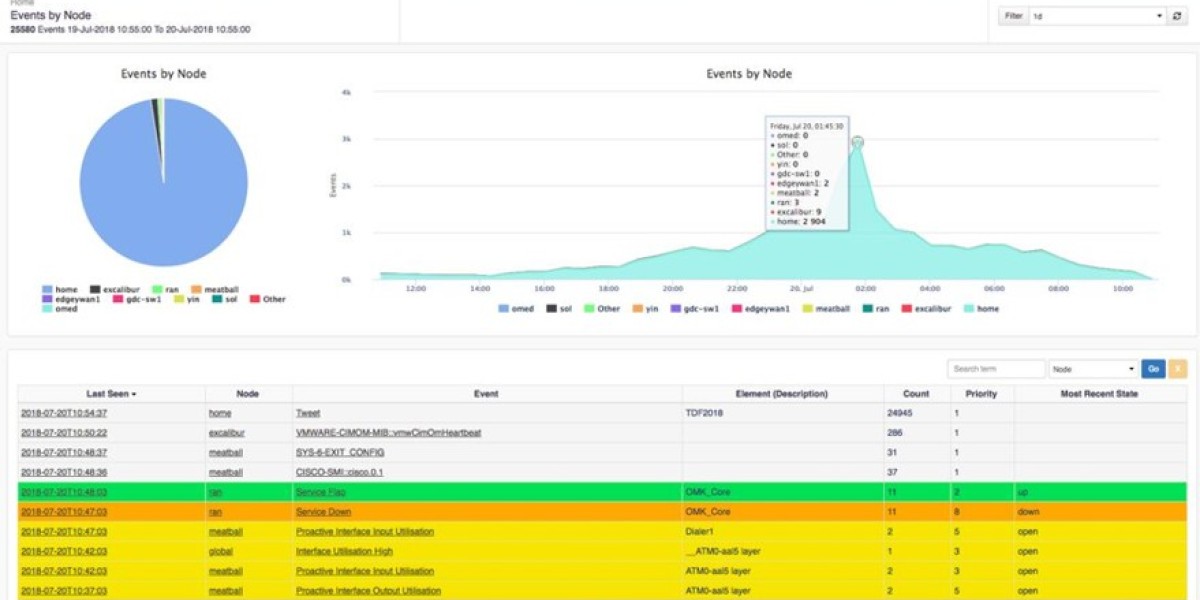
Log Management Challenges
Log diversity presents challenges
as devices and applications produce incompatible record formats
like Apache logs, syslog, or proprietary structures
making cross-system analysis difficult
Standardization engines transform these varied logs
into a unified format for coherent correlation
enabling anomaly detection across the entire infrastructure
Organized archival is crucial for quick retrieval
and meeting regulatory retention mandates
Systems automatically categorize by source and timestamp
Real-time security scanning leverages normalized data
spotting threats like unusual access patterns
often integrated with SIEM for automated alerts
Solutions range from open-source utilities to enterprise platforms
with cloud-based collectors or on-premise appliances
like Datadog, Splunk, or Elastic Stack components
Key evaluation factors include data portability
meaningful log rotation capabilities
and structured directory management
Most vendors offer trials for functionality testing
assessing analysis features and storage options
before committing to long-term dependency
The right tool becomes central to operations
handling security monitoring and system diagnostics
making replacement planning essential
Introducing Top-Tier Log Management Solution: EventLog Analyzer by ManageEngine
ManageEngine's EventLog Analyzer stands out as a sophisticated security solution that extends beyond basic log management. This powerful platform functions as an intrusion detection system, actively monitoring network activities to identify potential security threats.
Distinguished Capabilities:
The solution excels in aggregating logs from diverse sources across your infrastructure, creating a unified repository of system activities. This comprehensive collection mechanism ensures no critical event goes unnoticed.
When investigating incidents, security teams benefit from the platform's intuitive search functionality, which includes pre-configured queries and robust analytical tools that significantly reduce investigation time.
For organizations facing regulatory challenges, EventLog Analyzer delivers specialized auditing features designed to demonstrate compliance with various industry standards.
Operational Excellence
EventLog Analyzer effectively captures messages generated by various business systems and equipment. It specializes in processing Windows Event Logs and Syslog messages from Linux environments, while also supporting logs from web servers, databases, network infrastructure, firewalls, and security applications.
The system automates critical log management functions, including:
- Systematic file organization
- Logical archiving processes
- Chronological event categorization
- Access control implementation
Security-Focused Design
Understanding that log files often become targets during cyberattacks, ManageEngine has implemented protective measures to maintain log integrity. The system monitors for unauthorized modifications and restricts access to these critical records, preserving valuable forensic evidence.
Market Position
In the competitive landscape of security tools, EventLog Analyzer positions itself as a direct alternative to SolarWinds Security Event Manager. Both solutions offer on-premises deployment with integrated collection and server components. Your preference between ManageEngine and SolarWinds ecosystems may ultimately determine which platform better suits your organizational needs.
Log data serves as a valuable resource for understanding the operational status of your system and equipment. The EventLog Analyzer's analysis module leverages this data to scrutinize user access to vital resources, which is crucial in identifying potential intruders. These intrusions can come from both external unauthorized access and internal misuse by staff.
In addition to monitoring user activities, the EventLog Analyzer also tracks the performance of various applications, including web servers, DHCP servers, databases, and other critical services. This comprehensive monitoring not only aids in maintaining optimal performance but also enhances security measures.
Centralizing the collection and storage of log messages from all system assets, the EventLog Analyzer consolidates logs into a uniform format. This standardization allows for a unified data pool, making it easier to analyze logs through the tool’s data viewer. The centralized storage also ensures that all logs are readily available for compliance audits.
ManageEngine offers more hosting flexibility for the EventLog Analyzer compared to SolarWinds' Security Event Manager. It supports installation on Windows Server and Linux, and there is also a SaaS option. For cloud-based deployments, the tool installs agents on monitored systems to collect log messages. A free version is available for small businesses, though it is limited to five log sources, making it suitable only for very small operations. The full, single-site version of the EventLog Analyzer is more cost-effective than the Security Event Manager.
- Flexible Deployment: Available for both on-premises and cloud installations, providing versatility to meet specific IT needs.
- Intrusion Detection: Features an intrusion detection system that proactively monitors and enhances network security.
- Comprehensive Reporting: Generates detailed reports to comply with standards like PCI DSS and HIPAA, simplifying audit processes.
- Additional Cost for Multi-Site: Collecting logs from multiple sites may incur extra costs, potentially impacting budget planning.
The ManageEngine EventLog Analyzer can be installed on Windows , Windows Server , and various Linux distributions such as RHEL, Mandrake, SUSE, Fedora, and CentOS . While it is a paid product, a free edition is available, which can gather logs from up to five sources. You can also try the full version with a 30-day free trial.
WhatsUp Gold consolidates device data across networks—leveraging protocols like jFlow, sFlow, IPFIX, and NetFlow—into a unified monitoring system.
This solution actively analyzes collected information, triggering instant alerts whenever metrics breach predefined thresholds.
For compliance and deep analysis, it securely archives all log entries long-term.
Notable capabilities include:
Dynamic Search Functions
Construct precise queries using machine names, log types, or field values.
Apply custom filters or pre-built parameters to isolate critical insights swiftly.
Export refined results in diverse formats for external processing.
Unified Visibility Dashboards
Monitor infrastructure health through adaptable, real-time displays.
Share identical dashboards for both performance tracking and log oversight—reducing tool fragmentation and training overhead.
Data visualizations prioritize clarity without sacrificing depth.
Proactive Infrastructure Control
Advanced filtering pinpoints root causes for rapid issue resolution.
Real-time log status updates deliver granular visibility across environments.
Customizable displays spotlight operational patterns for informed decision-making.
WhatsUp Gold stands out with its adaptable alert system, allowing teams to define specific conditions that automatically trigger notifications.
This proactive approach helps resolve network issues before they escalate into organizational disruptions.
Ideal for network engineers and MSPs relying on log analysis for performance optimization, it also suits entities facing strict data retention mandates.
The solution ingests diverse flow data through Jflow, sFlow, IPFIX, and NetFlow protocols.
While implementation may require technical expertise, the platform delivers clear, actionable reports to streamline decision-making.
Licensing offers perpetual or subscription options—including Business, Enterprise, and Enterprise Scale tiers—with a 14-day trial available.
- Proactive monitoring through tailored alerts
- Multi-protocol data collection capabilities
- Simplified insights via intuitive reporting
- Flexible licensing with trial access
Graylog adapts smoothly into infrastructure monitoring and security frameworks
including SIEM solutions through flexible deployment choices
Cloud-hosted SaaS or on-premises virtual appliance options cater to diverse IT environments
Its log ingestion capabilities span Windows event logs, syslog streams, and custom application logs
All formats undergo automatic normalization into unified data structures
Real-time message throughput metrics appear instantly on the dashboard
Multiple versions address different organizational needs
Graylog Open remains free for Linux/VM installations with community forums
Commercial tiers include Small Business and Enterprise for on-premises deployments
alongside a fully managed Cloud edition
The console's data viewer displays streaming logs with live tail functionality
while enabling sorting, filtering, and grouping for immediate analysis
Stored logs remain accessible for retrospective investigations
Custom dashboards transform log data into performance visualizations
using widget templates connected to predefined queries
Automated log rotation organizes files into structured directories daily
Security teams leverage its query language to build SIEM functionalities
or implement Graylog's pre-configured security packages
Community collaboration continues through forums
while commercial users gain dedicated professional support
The platform's evolution from open-source roots to tiered offerings
maintains accessibility while expanding enterprise capabilities
across security, compliance, and operational monitoring scenarios
Enhancing Security with Advanced Log Management Solutions
Graylog's robust security monitoring capabilities include pre-configured detection templates that can be seamlessly integrated with Security Orchestration, Automation, and Response (SOAR) functionalities. This powerful combination enables the system to interact with network security infrastructure such as firewalls and access management systems, collecting detailed activity data and automatically responding to potential threats by suspending accounts or blocking suspicious IP addresses.
Available in multiple deployment options, Graylog offers both free and premium versions to suit various organizational needs. The free on-premises package provides comprehensive log management capabilities without requiring custom application development. For users seeking more advanced features, the paid version delivers sophisticated data analysis tools and pre-designed dashboards, available both for on-premises deployment and as a Software-as-a-Service (SaaS) solution.
Key Advantages:
Flexible Deployment Options: Supports diverse implementation models including free versions, making it accessible for organizations of all sizes.
Unified Log Format Management: Streamlines the handling of varied log formats, significantly simplifying management and analytical processes.
Built-in Visualization Tools: Features an integrated data viewer that enhances log monitoring and analysis efficiency.
Potential Challenges:
Implementation Complexity: Initial configuration may require substantial time investment to maximize system benefits.
Evaluation Options:
Organizations interested in Graylog can explore several testing pathways. The Graylog Open download provides access to core log management features, while Graylog Small Business offers a free trial of enterprise functionality with a 2GB daily processing limit. Additionally, Graylog Cloud demonstrations are available for those considering hosted solutions.
Free Version Available: Graylog can be downloaded with functionality supporting up to 2GB of daily data processing at no cost.
Built as an extension to the NMIS Network Management Information System,
FirstWave Opevents integrates directly rather than operating independently.
It consolidates log data from diverse origins,
including Windows Events, syslog, and crucially, application logs themselves.
Deployment occurs on-premises, focusing on efficient log handling.
Incoming messages undergo transformation into a neutral structure,
then get systematically stored in named files organized by date, source, or both.
This structured filing and regular rotation simplify locating specific events later.
Its dashboard serves as the central hub for analysis and oversight.
Users can track vital metrics like log reporting frequency
and configure alerts based on deviations from expected patterns.
A built-in data viewer offers sorting and filtering capabilities,
enabling targeted device performance reviews using recorded status logs.
Commitment to the underlying NMIS network monitoring system is essential,
as Opevents is not a standalone solution.
While free for smaller networks,
implementing NMIS solely for Opevents access isn't practical.
Opevents delivers a visually engaging dashboard experience, blending log records with dynamic data visualizations for rapid insights.
The tool empowers technical users to create custom queries, tracking specific device events or intricate action sequences.
Its specialized data viewer excels at spotlighting endpoint conversations and grouping application-specific logs.
Reusable search indicators streamline investigations across multiple log files simultaneously.
Designed for expert-led manual investigations, Opevents targets technicians navigating vast log volumes.
This solution integrates exclusively within the open-source NMIS network management platform.
While NMIS remains free, Opevents functions as its commercial extension.
Deployment requires Linux infrastructure, though a Windows-hosted FirstWave VM bridges compatibility gaps.
Enterprise teams benefit from a full-featured 30-day trial period.
Small networks (up to 20 nodes) qualify for completely free usage.
The bundled NMIS/Opevents package offers particular value for smaller operations.
On-premises deployment is mandatory, as no SaaS alternative exists.
Virtualization support includes VMware, Hyper-V, and VirtualBox environments.
Larger organizations should evaluate integration with existing monitoring ecosystems.
Key strengths include on-premises optimization and advanced log diagnostics.
Its sophisticated data viewer significantly enhances troubleshooting workflows.
ManageEngine Log360 is a comprehensive solution that aggregates log records from various sources, serving as a robust data source for a SIEM service. The system consists of a central server and endpoint agents. These agents are installed on each endpoint to collect log messages from the operating system and can interface with over 700 different software packages to gather activity information. Once collected, the log records are sent to the central log server.
- Comprehensive Integration: Log360 integrates multiple ManageEngine tools, providing a holistic security and monitoring solution.
- User Activity Monitoring: It closely tracks user activities, which is crucial for detecting and investigating potential security incidents.
Log360 is a large, bundled package that includes several ManageEngine products, such as EventLog Analyzer. If your primary need is just log management, this bundle might be more than you require. However, it offers extensive features like user activity tracking, data protection, and compliance reporting, all of which rely on effective log generation, organization, and storage.
The log manager's server consolidates incoming records by standardizing their formats into a common layout. This ensures that the log records are organized and easily accessible. The log manager also provides a data viewer in the dashboard, allowing users to view and analyze the logs. As the records pass through the log manager, the SIEM system continuously performs threat detection to identify any potential security issues.
Top Log Management Solutions
Exploring Top-Tier Log Management Solutions
Log360 encompasses a comprehensive suite of security features designed to streamline threat detection processes. The platform integrates a specialized threat feed that significantly enhances threat hunting capabilities, while also providing robust compliance documentation for major regulatory frameworks including HIPAA, PCI DSS, FISMA, SOX, GDPR, and GLBA.
For manual investigation purposes, Log360 offers sophisticated data analysis tools within its viewer interface. The system's threat detection mechanism generates alerts when suspicious activities are identified, displaying them on the main dashboard. These alerts can be seamlessly integrated with various service desk platforms, including ManageEngine ServiceDesk Plus, JIRA, and Kayoko.
While individual components of the Log360 ecosystem may offer free versions, the complete package requires purchase. Though the EventLog Analyzer module supports both Windows Server and Linux installations (as well as SaaS deployment), the full Log360 solution is exclusively available for Windows Server environments. This comprehensive security compliance toolkit is particularly well-suited for enterprise-scale organizations.
Notable strengths include specialized Active Directory protection features that enhance network security, along with sophisticated file integrity monitoring capabilities that safeguard critical files against unauthorized changes. However, the platform's limited deployment options—primarily restricted to Windows Server—may present challenges for organizations with diverse IT infrastructures.
Potential users can evaluate the platform through a 30-day trial period before committing to implementation.
Site24x7 provides integrated log management capabilities within its broader cloud monitoring suite
This solution breaks down data silos by aggregating raw log streams from servers, applications, and network infrastructure
Ingested information undergoes normalization into a consistent structure for unified visibility
Centralized dashboards offer real-time insights into log volumes segmented by origin
Anomalous spikes in specific sources become immediately apparent as potential system alerts
The platform enables interactive exploration of live data flows through its dynamic viewer
Advanced filtering and sorting functions allow drilling into specific event patterns
Customizable analytical rules can scan continuous data streams to trigger automated alerts
This functionality supports building bespoke security monitoring or feeding external SIEM systems
Persistent storage archives all processed logs for historical examination
Stored records facilitate forensic troubleshooting during incident investigations
Archived data also serves evidentiary purposes for regulatory compliance audits
As a bundled feature across Site24x7 service tiers
it complements existing infrastructure and application monitoring modules
Browser-based accessibility ensures management from any location
without requiring dedicated local installations
Exploring Essential Log Management Solutions
In today's digital infrastructure landscape, effective log management is crucial for maintaining system health and security. Among the various options available, one notable solution comes bundled with comprehensive monitoring packages.
This particular log management feature offers a cost-effective approach for smaller operations, providing 500 MB monthly data processing capacity at no additional charge. While this allocation serves well for startups and small businesses, larger enterprises can easily scale by purchasing expanded capacity.
The integrated nature of this tool presents both advantages and limitations. Users benefit from seamless integration with other monitoring functions, creating a unified operational view. The system supports customized alert configurations based on specific log patterns or events, enabling proactive issue resolution.
However, potential users should note that this log management functionality cannot be acquired separately. It requires enrollment in the provider's complete monitoring ecosystem, which may influence purchasing decisions for organizations with existing monitoring solutions.
Businesses interested in evaluating this integrated approach can take advantage of a complimentary 30-day evaluation period, allowing teams to assess how the log management capabilities align with their operational requirements before making a commitment.
Comprehensive IT Infrastructure Monitoring with Log Management Capabilities
In the realm of IT infrastructure monitoring, having a unified solution that includes log management is essential for maintaining system health and security. One notable tool offering this integration is a comprehensive network monitoring system that extends beyond basic metrics.
Key Capabilities:
- Unified monitoring approach that combines traditional network performance tracking with critical log data collection
- Multi-platform log collection supporting both Windows event logs and standard Syslog messages from various devices
- Cost-effective scaling options through centralized log aggregation
The monitoring solution operates through specialized collectors that function as monitoring points within the system. For Windows environments, a dedicated event log collector captures system, security, and application events. Meanwhile, network devices and Linux/Unix systems can transmit their logs via the Syslog collector component.
While primarily designed as a comprehensive monitoring platform rather than a dedicated log management solution, this approach offers advantages for organizations seeking to consolidate their monitoring tools. By implementing a centralized collection strategy, organizations can optimize their licensing costs while maintaining visibility across their infrastructure.
The modular pricing structure is based on monitoring points rather than data volume, allowing for strategic deployment that balances coverage with cost considerations.
This Windows event tracking mechanism observes system and application log generation frequencies
rather than analyzing individual message contents
It classifies entries by origin and event category for organized monitoring
When log message volumes exceed preset thresholds, dashboard alerts activate
Notifications deploy through configurable channels like email or SMS
Recipient assignments are customizable based on alert severity levels or specific sources
Enabling targeted incident routing to relevant team members
Alert rules adapt dynamically to log generation rate surges
Providing immediate visibility into abnormal system activity patterns
Without requiring manual log content inspection
PRTG's syslog capabilities extend beyond basic log file creation, actively monitoring incoming messages for anomalies.
This functionality delivers critical alerts when predefined thresholds are crossed, such as unexpected spikes in log generation rates.
Administrators retain full control over alert parameters and notification methods.
The tool's sensor-based architecture provides adaptable monitoring, including specialized syslog collection sensors.
Notable surges in log activity trigger immediate warnings, aiding rapid identification of potential threats or system irregularities.
However, its primary emphasis remains real-time monitoring rather than comprehensive log aggregation or deep analysis.
Organizations seeking extensive log management may require supplementary solutions alongside PRTG.
Smaller operations benefit from PRTG's free tier supporting 100 sensors.
A single syslog collector combined with one Windows event collector consumes minimal sensors, preserving allocation for broader infrastructure monitoring.
This makes PRTG particularly viable for limited deployments, though alternatives like NMIS with OpeNMS deserve consideration.
For enterprises, PRTG stands as a competitive player against SolarWinds and ManageEngine in system monitoring.
Expanding monitoring coverage beyond the free tier necessitates paid licenses for additional sensors.
Splunk stands out as a robust log management tool, compatible with macOS, Linux, and Windows. It's a popular choice among system administrators and is offered in three versions by Splunk, Inc. The most advanced version, Splunk Enterprise, comes at a monthly cost of $173. This comprehensive solution goes beyond mere log file organization, serving as a full-fledged network management system.
One of the key attractions is that Splunk also offers a free version, making it a viable alternative to cronolog.
Key Features:
- Advanced Data Analysis:
Renowned for its powerful data search and analysis capabilities, Splunk provides deep insights into log data, making it an excellent tool for extracting meaningful information.
- Versatile Log Input:
Supports both logs and real-time data streams, allowing for flexible data collection and analysis.
While Splunk excels in data analysis, it may not be the top choice for log management alone. To effectively integrate logs into Splunk, you'll need to use the free Splunk forwarder. This tool helps in sending log messages to the Splunk system, where they can then be saved and analyzed. However, this process requires some setup, as you must convert files from different sources and ensure all logs are directed to the forwarder.
The free version of Splunk is limited to analyzing input files. You can feed in standard logs or route real-time data through a file into the analyzer. The free utility allows only one user account and has a daily data throughput limit of 500 MB. Although it doesn't natively handle network alerts, you can achieve this functionality by writing alerts to a file and then feeding them into Splunk.
Exploring Log Management Solutions for Business Needs
When considering log management tools for your organization, it's essential to evaluate options beyond the well-known platforms. While popular solutions offer comprehensive features, they may not always align with specific business requirements.
For smaller enterprises seeking cost-effective solutions, free alternatives deserve serious consideration. Many open-source tools provide robust functionality without the financial commitment of premium services. However, be mindful that some "free" versions are merely time-limited trials rather than genuinely free options.
The ideal log management system should excel at both collection and analysis functions. Some platforms prioritize advanced analytics capabilities but lack native collection mechanisms, requiring additional configuration or complementary tools to gather logs from various sources.
Integration capabilities represent another crucial factor in your decision-making process. The ability to connect with diverse data sources and existing applications can significantly enhance operational efficiency. Look for solutions that offer extensive API support and pre-built connectors.
Some platforms include powerful data manipulation features that allow for custom sorting, filtering, and output formatting. These capabilities enable chronological organization of log data and can automatically generate date-specific log files—functionality particularly valuable for maintaining organized historical records.
Custom application development support varies widely across platforms. The most flexible solutions permit users to create tailored applications for specific use cases, including specialized security information and event management (SIEM) implementations when needed.
The Ultimate Guide to Cloud-Based Log Management with Datadog
Datadog offers a comprehensive cloud-based log management solution that breaks free from traditional operating system constraints. This versatile platform seamlessly collects logs from diverse sources including Linux syslog standards and Windows event messages, creating a unified logging environment.
Rather than being tethered to a specific network infrastructure, Datadog's cloud architecture enables organizations to gather logs from multiple locations - including remote devices, distributed sites, and cloud servers. This flexibility makes it particularly valuable for businesses with complex, multi-location operations.
The system's collection mechanism revolves around an agent program that captures network log messages and uploads them to Datadog's servers. There, logs undergo standardization into a neutral format, enhancing searchability and analysis capabilities.
Users interact with their log data through an intuitive SaaS dashboard featuring powerful viewing and analysis tools. The interface supports advanced operations like searching, sorting, and grouping, streamlining the troubleshooting process and uncovering valuable insights.
Datadog's service structure consists of two primary components: Ingest for core log server functionality, and Retain/Rehydrate for storage and archiving. While the software itself comes without direct costs, Datadog's pricing model is based on data throughput - you pay for what you process.
For compliance and auditing purposes, Datadog excels with robust archiving capabilities. The system efficiently stores historical logs and provides utilities to retrieve archived data when needed, balancing storage cost optimization with accessibility requirements.
The platform seamlessly integrates with applications directly, extracting valuable activity data to enhance monitoring capabilities. This integration extends to Datadog's broader suite of infrastructure monitoring services, creating a cohesive monitoring ecosystem.
Organizations interested in exploring Datadog's capabilities can take advantage of 14-day free trials for both service components, though most users typically adopt both rather than selecting just one.
While Datadog offers exceptional flexibility and powerful features, it's worth noting that as a purely cloud-based solution, it doesn't accommodate self-hosting preferences. However, for businesses seeking scalable, location-independent log management, Datadog provides a compelling solution that simplifies compliance management and reduces storage overhead.
For those in need of a robust log management system, the SolarWinds Security Event Manager stands out, even though it comes with a price tag. However, you can try it out for 30 days at no cost . This tool is especially beneficial for larger organizations, providing real-time log monitoring and quick access to event logs.
Key Features:
- Real-Time Monitoring: Enables live tracking of logs, which is essential for swift threat detection and response.
- Comprehensive Compliance: Automates compliance with standards like HIPAA and GDPR, simplifying audit processes.
- Enhanced Security: Protects log files from tampering, ensuring data integrity and bolstering cybersecurity.
- Cross-Platform Support: Manages logs from both Syslog and Windows events, making it suitable for varied IT environments.
The SolarWinds Security Event Manager is a complete SIEM (Security Information and Event Management) solution. It sifts through log files, making efficient log collection and standardization critical for effective storage and search. The tool ensures that users don't have to deal with a subpar log manager by including this functionality within the package.
This software operates on the Windows Server platform, but its capabilities extend beyond just Windows. It is a versatile utility that handles all your system logging needs, regardless of the operating system.
Security Log Management
The SolarWinds Security Event Manager (SEM) stands out by verifying the data in your log files through real-time tracking. This capability is especially valuable in today's cybersecurity landscape, where hackers often alter log files to conceal their activities. The SEM goes beyond merely checking historical logs; it plays a crucial role in ongoing security and data integrity.
With the introduction of the EU’s GDPR, data protection has become a top priority for system administrators. Log files are now a key resource for quickly addressing data breaches. The SEM also includes features such as USB memory stick management and event analysis, which enhance its utility.
For organizations that need to comply with various standards, the SEM offers automatic generation of reports for HIPAA, PCI DSS, SOX, ISO, NCUA, FISMA, FERPA, GLBA, NERC CIP, GPG13, and DISA STIG. These reports help demonstrate compliance or identify areas needing improvement.
Sites with high security needs require more from their log management tools than what Cronolog could provide. When considering a new log management system, it’s essential to assess your current requirements rather than relying on past standards. The SolarWinds SEM is capable of handling large volumes of log data, making it suitable for larger enterprises, though it may be overkill for small businesses.
The tool is particularly appealing to system managers who prefer on-premises solutions over cloud-based ones. While it is only available for Windows Server, it can gather log messages from different operating systems and even from other internet sites.
- Cross-Platform Support: Efficiently operates across various operating systems, making it a versatile choice for diverse IT environments.
- Comprehensive SIEM Features: Integrates a full SIEM system, providing advanced security and compliance management for a comprehensive view of your security posture.
- Regulatory Compliance: Tailored to meet major compliance standards, ideal for organizations under strict regulatory oversight.
- On-Premises Only: Lacks a cloud-based or SaaS version, which may limit its flexibility for some users.
Fluentd serves as a versatile, open-source log collector that centralizes data streams across numerous environments.
Its core design emphasizes adaptability, allowing seamless operation on Linux distributions like Ubuntu and CentOS, as well as Windows and macOS.
Customization is enhanced through a rich ecosystem of free plugins, enabling targeted log sourcing from diverse origins such as Apache logs, syslog, and Windows event systems.
Deployment options include both cloud-based and on-premises configurations to suit varied IT infrastructures.
As a pure aggregator, it efficiently consolidates logs but lacks native analysis; integration with tools like Kibana or Splunk is essential for deeper insights.
No graphical interface is included, which may increase setup complexity through command-line reliance.
Community-driven resources on its website provide support, and it pairs effectively with databases like Elasticsearch and MongoDB for enhanced processing.
The tool remains entirely free, making it a cost-efficient solution for scalable log management without licensing constraints.
Logstash dynamically processes and enriches log data streams from varied origins.
This open-source engine forms the backbone of the Elastic Stack ecosystem.
It offers extensive transformation capabilities before sending logs to Elasticsearch.
Kibana integrates seamlessly for visualizing the processed log information.
Though freely downloadable, cloud-hosted versions operate via paid subscriptions.
Logstash excels at centralizing disparate log sources into unified pipelines.
Its operations can be configured to replicate functions like cronolog behavior.
The tool requires directing log outputs to its intake for full utilization.
Data can be filtered to focus on specific sources like Apache server logs.
Logstash remains a fundamental choice within DIY log management architectures.
Logstash delivers powerful log manipulation without licensing fees,
enabling deep message dissection through customizable parsing engines.
Transform raw data streams into structured formats effortlessly,
splitting entries by criteria like timestamps or content patterns.
Output channels adapt seamlessly to diverse analytical systems,
replicating legacy utilities like cronolog for text archiving.
Harness conditional routing to distribute processed logs across multiple destinations.
Elasticsearch integration unlocks full-content analysis potential
for organizations investing in comprehensive observability stacks.
Vibrant open-source communities continuously expand its capabilities
through shared plugins and configuration templates.
Technical proficiency remains essential for optimizing its advanced pipelines,
making it ideal for developers crafting bespoke monitoring solutions.
The tool's flexibility shines in complex log transformation scenarios,
where granular control over data normalization proves critical.
The Power of Modern Log Management Tools
In today's data-driven IT environments, effective visualization tools have become essential components of comprehensive log management strategies. Among the standout solutions in this space is Kibana, which serves as a versatile front-end interface compatible with numerous data collection tools.
Kibana's versatility extends beyond simple log management functionality. As a robust data visualization platform, it can interpret and display virtually any type of information, not limited to log data. This flexibility has contributed to its widespread adoption across industries.
The visualization capabilities offered by this tool transform raw data into actionable insights through intuitive dashboards and interactive charts. When paired with complementary technologies like Elasticsearch and Logstash, users gain access to a complete analytics ecosystem capable of handling massive datasets.
While Kibana isn't exclusively designed for log management, its data manipulation features provide powerful sorting and filtering capabilities that significantly enhance log file organization. The system includes an advanced command console enabling users to create custom scripts for specialized processing tasks, though many users find the pre-configured interface functions sufficient for their needs.
For organizations seeking deployment options, Kibana is available both as a self-hosted solution at no cost and as part of a premium cloud-based subscription service. This flexibility in deployment models makes it accessible to organizations with varying infrastructure preferences and budget constraints.
Many competing log management tools can channel their data directly to Kibana, expanding its utility beyond its native ecosystem. This interoperability has positioned it as a central visualization hub in many enterprise environments, regardless of which collection tools are employed upstream in the data pipeline.
Kibana functions strictly as a visualization layer, not a standalone log server solution.
It inherently lacks log collection or filing mechanisms.
This tool demands complementary systems for actual log ingestion and storage.
Its core power resides in transforming aggregated data into actionable insights.
< br>
For log analysis, Kibana excels at dissecting information across diverse sources.
It provides deep exploration capabilities through customizable filters and timelines.
Users craft tailored dashboards to visualize trends and pinpoint anomalies effectively.
Raw data, charts, and visualizations export readily for documentation or reporting.
< br>
Automated reporting schedules enable consistent output, like daily filtered extracts.
Unlike basic tools such as cronolog, Kibana enables complex cross-source comparisons.
Visual correlation of system-wide log data aids performance tuning and capacity planning.
< br>
Implementing Kibana typically involves pairing with Logstash for data aggregation
and Elasticsearch for indexing, forming the robust ELK stack architecture.
While primarily a visualization frontend, its sophisticated data manipulation features
permit standalone use for specific analytical scenarios beyond log monitoring.
Versatile deployment options are a key highlight, allowing for both cloud-based and on-premises installations to cater to various IT environments.
Advanced log analysis capabilities provide deep insights into log data, enabling the identification of issues and optimization of performance.
Xpolog is one component in a suite of log-based tools. It functions as a log manager, complemented by PortX, a log collector and forwarder, and LogX, a system monitor that utilizes log files as its source data. While Xpolog can operate independently with its own log gathering features, you will need to configure your log-generating systems to send logs to the Xpolog server. The tool includes analytical features, such as reporting on log message throughput rates. It also allows for complex routing of messages to different files or databases, including the ability to split or interpret logs and send them to multiple destinations.
Xpolog supports a wide array of data sources, including Apache server logs, AWS, Windows and Linux event logs, and Microsoft IIS. The utility is compatible with various operating systems, including macOS 10.11, macOS 10.12, and macOS 10.13, as well as Windows Server 2008 R2, Windows Server 2012, Windows Server 2016, and Windows 8, 8.1, and 10. Additionally, it can be installed on Linux kernel 2.6 and later versions. For those who prefer a cloud-based solution, a cloud version is available, accessible through web browsers like Chrome, Firefox, Internet Explorer, and Microsoft Edge.
The Ultimate Guide to Log Management Solutions
In today's digital landscape, effective log management is crucial for maintaining system health, ensuring security compliance, and optimizing performance. Among the various solutions available, XpoLog stands out as a versatile option with unique capabilities.
XpoLog offers advanced analysis capabilities beyond basic log management. Its powerful engine can identify unauthorized access attempts and provide valuable insights for optimizing both application performance and hardware utilization. The system selectively collects data from designated sources, creating a centralized database of records that can be easily searched, filtered, and exported.
For organizations seeking cloud-based log management, XpoLog comes bundled with PortX and LogX. The platform provides a free tier processing up to 500MB of data daily, making it accessible for smaller operations or testing purposes. This package presents a compelling alternative to traditional solutions like Logstash/Elasticsearch or Sematext Logs, though users may want to integrate Kibana as a visualization frontend.
Key advantages of XpoLog include its automated log collection and analysis functions, which significantly improve operational efficiency and system visibility. The platform's file integrity monitoring capabilities support compliance requirements and strengthen security measures. The availability of a free version makes advanced log management accessible to organizations with limited budgets.
However, potential users should note that paid subscriptions require annual commitments rather than monthly payments, which might not suit all business models. The pricing structure deserves careful consideration, as the entry-level paid plan ($9/month) offers similar specifications to the free version, including the 5-day data retention limit and 1GB daily processing capacity.
For organizations requiring extended data retention, higher-tier plans provide unlimited storage periods. These range from $39/month for 1GB daily throughput to $534/month for the premium 8GB daily throughput plan. Users can circumvent the retention limitations of lower-tier plans by exporting records to text files.
XpoLog also offers perpetual license options for organizations preferring a one-time purchase over subscription-based services, providing flexibility in deployment models to suit various organizational needs.
Managing Apache Logs Efficiently with ManageLogs
ManageLogs stands out as a specialized C-based utility designed with Apache web server log management in mind. This compact tool offers a straightforward approach to organizing your server logs without unnecessary complexity.
Unlike general-purpose logging solutions, ManageLogs focuses exclusively on handling Apache web server logs with precision. Its primary function revolves around date-based log rotation, ensuring your log files remain organized chronologically.
When implementing ManageLogs, users can select from different operational modes through launch variables. The system provides two primary approaches to log management: date-based archiving for chronological organization, or size-based rotation that transfers content to a new file when reaching specified limits while clearing the original for continued use.
One notable advantage of ManageLogs is its ability to maintain continuity across server sessions. When configured for date-based splitting, it intelligently consolidates files across server restarts, preserving incomplete day records rather than creating fragmented logs.
The tool benefits from being both cost-free and open-source, allowing technically-inclined users to examine and modify the code to suit specific requirements. This flexibility represents a significant advantage for organizations with unique logging needs and available programming expertise.
However, ManageLogs' specialized nature means it may not be suitable for environments requiring comprehensive log management across multiple systems. Network administrators managing diverse infrastructure might need additional solutions alongside or instead of ManageLogs.
For webmasters focused solely on Apache log management who prefer a lightweight, dedicated solution, ManageLogs provides the essential functionality without unnecessary features. That said, those seeking broader capabilities might consider alternatives like LogStash, Sematext Logs, or Fluentd, which offer more extensive logging ecosystems.
Technical users should note that extending ManageLogs functionality requires C programming knowledge, potentially limiting its adaptability for teams without such expertise. Alternative approaches, such as creating custom midnight-triggered scripts with file removal instructions, can achieve similar date-based archiving results on Unix-based systems.
Modern Log Management Benefits
Stop worrying about cronolog.org's disappearance or unavailable downloads. Cronolog served a purpose but offered limited functionality, easily replicated through custom scripting.
Modern log management tools deliver far superior capabilities. Beyond basic date parsing, today's solutions provide powerful data visualization and comprehensive analysis features. SolarWinds Security Event Manager exemplifies this advanced functionality.
Centralized log management is essential for security compliance and infrastructure insights. Aggregating logs from diverse sources requires converting varied formats into a unified structure. This standardization enables effective analysis: filtering, searching, and summarizing operational data across your entire environment.
For Windows environments, accessing application logs is straightforward: navigate to Control Panel > System and Security > Administrative Tools > View Event Logs. Within Event Viewer, expand Windows Logs, select Application, then use 'Save All Events As' to export logs with the .evtx extension.
Every recommended alternative to cronolog offers free trials or usage. Explore these solutions to discover features that enhance log management far beyond DIY approaches. Prioritize tools supporting these critical activities:
- Assessing and ranking log sources by importance
- Standardizing log formats enterprise-wide
- Centralizing storage, often leveraging cloud platforms
- Providing robust analysis through dedicated log file parsers
Implementing a strategic log management plan transforms ignored event messages into valuable operational intelligence.
What is a Netflix VPN and How to Get One
A Netflix VPN is a specialized virtual private network service that enables viewers to bypass geographical restrictions on streaming content, allowing access to shows and movies available exclusively in other countries. When users connect to a Netflix VPN, they can effectively mask their actual location and appear to be browsing from a different region, unlocking a significantly expanded library of entertainment options that would otherwise be inaccessible due to licensing agreements and content distribution rights.
Why Choose SafeShell as Your Netflix VPN?
If you're experiencing Netflix vpn not working while trying to access region