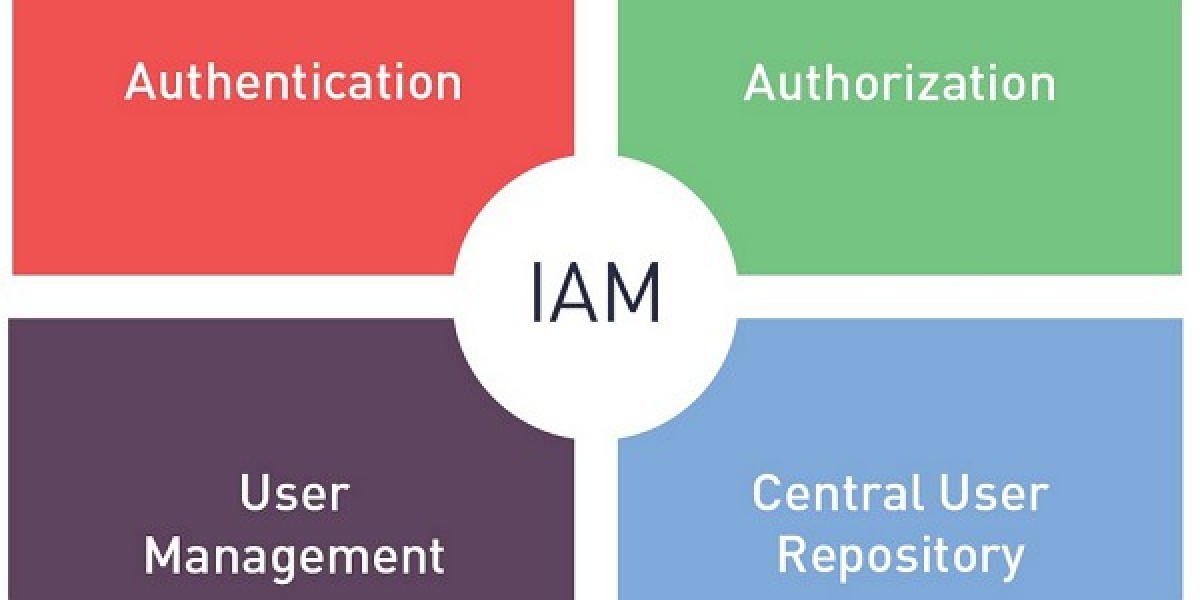
A practical Identity and Access Management Market Analysis focuses on how organizations choose IAM capabilities to reduce breach risk and meet compliance. The market includes access management (SSO, federation, MFA), identity governance (access reviews, role management), privileged access management, and customer identity platforms. Market analysis shows that adoption often starts with SSO and MFA because they deliver immediate security and user experience improvements. Organizations then expand into governance and PAM to address audit needs and high-risk admin access. Customer IAM adoption grows where businesses have large digital user bases and need scalable authentication and consent. Workload identity is a newer area, driven by cloud-native and microservice architectures. Market analysis also examines integration complexity, which is often the biggest barrier. IAM must connect to HR systems, directories, SaaS apps, and legacy systems, making implementation more about architecture and process than software selection alone.
Risk analysis highlights identity as a primary attack vector. Threats include phishing, credential stuffing, session hijacking, and insider misuse. Weak MFA choices, poor recovery workflows, and inconsistent policy enforcement can undermine protection. Market analysis emphasizes phishing-resistant MFA, conditional access, and least privilege as key mitigations. Another risk is operational: IAM outages can disrupt business by preventing logins, so high availability and disaster recovery are essential. Governance risks include overprovisioning and orphaned accounts, which increase breach impact and audit findings. PAM addresses high-risk admin privileges, but adoption can be difficult if workflows are too restrictive. Market analysis also considers privacy and consent risk in customer IAM, where data handling must meet legal requirements and user expectations. Integration and migration risk is another theme; consolidating directories or migrating to cloud identity can be complex and disruptive. Therefore, market analysis frequently recommends phased rollouts with pilot groups, careful policy tuning, and strong change management.
Adoption barriers include organizational silos and poor role design. IAM touches HR, IT, security, and business app owners, so governance requires cross-functional alignment. Role-based access control can fail if job roles are inconsistent or if exceptions are unmanaged. Access reviews can become checkbox exercises if not prioritized by risk and relevance. Market analysis therefore highlights the shift toward risk-based access governance, where reviews focus on privileged access and sensitive systems. Another barrier is user friction; overly strict MFA can cause pushback, leading to workarounds. Passwordless reduces friction but requires device readiness and strong recovery methods. Legacy apps can also be difficult to integrate with modern federation standards, requiring proxies or refactoring. Budget constraints may push organizations toward partial solutions that leave gaps. Vendor lock-in concerns influence decisions, especially for organizations adopting multi-cloud. Therefore, open standards, integration marketplaces, and data portability are important selection criteria in market analysis.
Forward-looking analysis suggests growth in unified identity platforms that combine access, governance, and privileged controls. Continuous risk scoring and behavioral analytics may help detect compromised accounts earlier. Workload identity and secrets management integration will expand as API-driven systems grow. Regulatory demands will increase focus on access logging, least privilege, and audit reporting. Market analysis indicates that differentiation will shift toward usability, automation, and trust: reducing friction while increasing security. Vendors that provide strong integration, high availability, and governance maturity will be favored. Organizations that treat IAM as a program—policy, process, and technology—will achieve stronger outcomes than those that treat it as a one-time implementation. The market analysis conclusion is consistent: IAM is foundational, but value depends on disciplined adoption and continuous improvement.
Top Trending Reports: